Phishing is a funny looking word with serious implications. But what is it? No, it has nothing to do with a ‘80s rock group or aquatic game. It refers to fraudulent electronic correspondence that attempts to steal personal information. These will often appear as though they were from a trusted source in hopes that you will let your guard down. No doubt you’ve probably heard a lot about it in the news recently. The number of major attacks is on the rise causing an estimated annual impact of $5 billion globally. So how do you avoid the proverbial hook? Don’t bite. Simple, right?
This is, of course, much easier said than done. The tactics and tools used by and available to these criminals are more sophisticated than ever before. Staying educated is key, so let’s take a look at some of the prevailing methods used in today’s phishing scams and what you can do to protect yourself.

In keeping with the theme, the first method is called spear phishing. This is the most basic and most common scheme present today. The “phisherman” will scour web pages, especially social media sites, for personal information. They will then use that to try and seem as legitimate as possible when contacting you. They may pose as a friend or family member, addressing you personally in the message while probing you for details.
The culprit may also try clone phishing. This method involves recreating a previously trusted message that contains some sort of link, which is made to look almost identical to the original. They’ll often send it from a similar looking email address in hopes that you won’t be able to tell the difference.
Most phishing attempts implement some form of link manipulation. Attackers will often try and trick you by sending links that appear identical to a trusted site. It may look something like this: “velocty.cu” as opposed to the actual site, “velocity.cu.” Some may use website forgery, creating fake login pages to steal your information as soon as you type it in. This might seem very difficult to avoid, but most browsers like Chrome, Safari and IE7, will alert you when foul play is afoot.
Perhaps the most nefarious method of phishing is called an evil twin scam. The hacker will set up a fake wireless network near a popular public hotspot, like hotels and coffee shops. Once you log on, fraudsters attempt to steal whatever they can. In cases such as these, it is important to pay close attention to the network you are signing into. In general, practice safe public surfing!

It’s easy at the end of a long day to gloss over links without thoroughly inspecting them, so stay sharp! The phisher relies on their victims overlooking tricks, so being wary is your best bet to avoid these scams. If an email from a friend or family member seems even slightly suspicious, call them up and ask if they actually sent the email. This goes for banks and other businesses as well. When following links within emails to outside websites, avoid clicking the link provided and manually navigate to the trusted site.
In this day and age, it is difficult to exist without having some sort of digital footprint. That does not mean that you can’t be cautious in what information you put on social media sites. Limiting what personal facts attackers have access to can go a long way to keep you out of their crosshairs.
Finally, and we can’t stress this enough, you should always use strong passwords. Using passwords that contain personal information, like birthdays and pet names, make it much easier for someone to crack your code.
So what is the takeaway here? Be suspicious! They can’t fool you if you’re paying attention. Armed with the knowledge of how these scammers work, all you need is a healthy level of skepticism. Stay sharp, click smart!
Check out the following image to get a better understanding of what a phishing scam might look like!
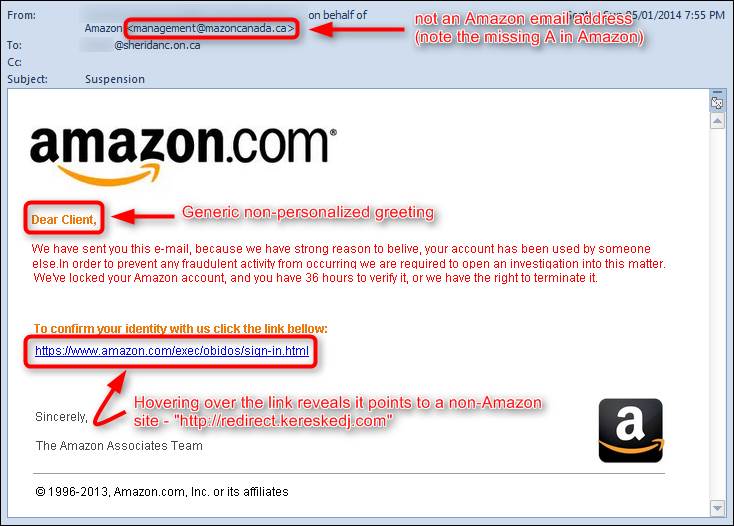
We hope that you found this information helpful! As always, if you have any further questions about this blog or any IT related inquiries, feel free to get in touch with us! Stay safe, stay Pretected.




