The issue
An exploit within Microsoft’s mail platform, Exchange, has been identified and has used by malicious parties that have resulted in tens of thousands of compromised servers. It is important to note that this vulnerability is isolated to companies and government agencies using self-hosted on premise Exchange server. The attackers discovered and started exploiting the vulnerability in January, but really picked up steam with a heavy attack in recent weeks. It allowed them to steal email contents by accessing the email server without a password.
What can be done?
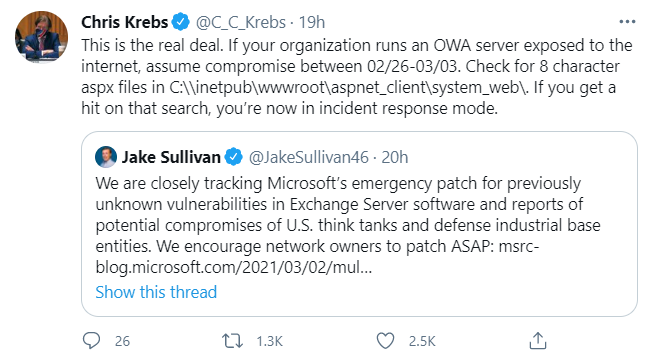
This kind of attack is referred to as a “zero-day” attack, in which Microsoft was unaware of the vulnerability. As of the writing of this article, Microsoft has released patches to fix the exploit, and it’s important to update as soon as possible. However, if you have a self-hosted on premise Exchange server, it is likely that it has already been compromised. Chris Krebs (former director of CISA) states on Twitter:
Microsoft’s Kevin Beaumont has released a tool available on GitHub that detects vulnerable servers. Your IT team should be able to run this to check your environment.
How do I protect my company in the future?
I do not mean to be doom and gloom, but in IT, it is not a matter of if, it is a matter of when and how bad. For instance, this zero-day attack compromised thousands of servers before Microsoft even knew it was an issue and started work towards patching. The only way to have avoided this compromise is by using a managed SaaS application, such as Microsoft365 (formerly Office365) or Google Workspace, instead of on-premise Exchange servers. These cloud based services have security closely managed by the provider, and are less likely to be compromised.
Still though, zero-day attacks can happen anywhere, so set yourself up for success with the following cyber security best practices:
– Patch Management Policies
– Password Management Policies
– Cyber Security Policies
– Business Continuity and Disaster Recovery
– Maintain UAC (User Account Control)
– 2 (or Multi) Factor Authentication
– Use a VPN
– DNS Filtering
– Use an Anti-Virus
– Encrypt all endpoints
– Train your employees
That last bit about training your employees will save you the most amount of time, money, and frustration. Over 90% of breaches occur due to phishing attacks. In other words, you can have all the high tech security in the world, but it won’t matter if someone just hands over the keys to the castle.
If you have any questions, Pretect is here to help. Our Managed IT Services can help support and protect your business with everything from 24/7 helpdesk support and cyber security, to training and awareness for your staff. We also offer Dark Web Monitoring (contact us for a free scan) and Phishing Simulations as part of our preventative protection.




