One moment, you’re happily browsing a trusted site. A few clicks later and Abracadabra! You’ve left the safety of the secured site and are now somewhere strange where pop-ups shout fake system messages at you. What happened? Maybe you clicked an advertisement, or maybe you simply saw one in the margins of your browser. “But this is a safe, secure site! What is this trickery?” you shout at your laptop. Something foul is afoot, but it isn’t magic. It’s Malvertising.
Advertisements have become a necessary evil in the online world. Most of us click passed them or employ some sort of adblocker to minimize our exposure. For many sites, however, advertising is often an essential component for staying in business. You likely know that sites like Youtube use advertising to make the majority of their revenue. What you may not have known is that advertisements are now a popular way for hackers to compromise your systems and data.
The practice of using advertisements as a conduit for malware attacks is known as malvertising. This method of misdirection has become increasingly popular following ransomware attacks, which caused many platforms to fortify certain security measures. Rather than attempting to install malicious software onto a target’s computer directly, this new wave relies heavily on URL redirection.

When you visit a site that is overtly suspicious (such as westealyourdata.com), you expect potential threats to spring from any link or ad. That is why you presumably avoid such sites. Malvertising, however, has now infiltrated the most trusted domains. One investigation revealed that a cabal of 28 “fake” ad agencies had been created all with the intent of injecting their infected ads into reliable web pages. How effective could this strategy be you ask? They accumulated one billion (yes, billion with a “b”) impressions last year.
This group, dubbed “Zirconium” by Confiant, used these agencies to forge relationships with legitimate intermediaries and trusted sites. Once they accomplished this, they were free to launch their redirection tactics. This simply means that clicking on an infected ad would take you from a trusted page to one that is free to run scripts, install software, and otherwise wreak havoc as they please.
A client of ours was searching a popular website for customer service contact information. On the page that listed the search results, an ad appeared that was disguised as a contact link. After clicking the incognito banner, our client’s browser was redirected to another site. They were immediately bombarded with pop-ups claiming that their computer was infected and gave a phone number for “support”. In situations like this, the hacker masquerading as a service representative hopes that the target will call. Then all they have to do is instruct their victim to unknowingly infect themselves. Fortunately, our client didn’t take the bait.
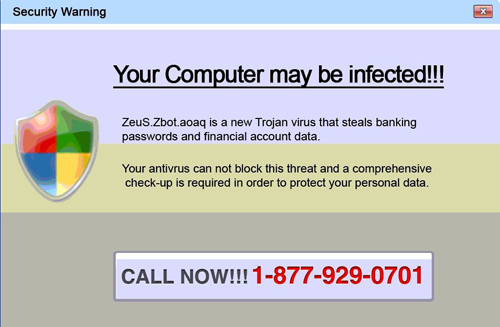
In our example, the attack didn’t result in any real damage. However, not all attacks are so easily avoided. That’s why it is important to take precautions to protect you and your company. Now that we’ve seen the hacker’s strategy, let’s look at a few ways you can fight back.
For starters, make sure that you and your employees have an ad blocker installed on your browser. Adblock Plus and uBlock are extensions and available for most browsers. It is a great first line of defense, but it is essential that you make sure to keep both your internet browser and plugins (like Adblock) updated. As mentioned earlier, though, many sites rely on advertisements for revenue. Consider whitelisting sites that you want to support, but always do so with caution.
It is also important that your computers are protected with some form of antivirus software. Not only will this help protect you from malvertising, but it also places a barrier between you and a host of other harmful programs. There are countless services that offer antivirus software, but we recommend setting up a consultation to make sure you are outfitted with the latest and greatest!
Finally, you can simply disable Javascript on your browser. This definitely depends on what it is you do on the internet; if your work routinely involves sites or applications that use Java, you’ll obviously need to leave it on. However, most of the time it isn’t a necessity. Make sure you consult your IT management team before taking this step.
The hackers of this world will always have new and innovative tricks up their sleeves. The best way to combat their efforts is to stay informed and partner with an experienced, reliable Managed Service Provider. Like Pretect! If you have issues with malvertising or are interested in taking steps to prevent it, give us a call. Until next time, stay safe!
If you would like to read a more extensive exploration of the Zirconium story, check it out here!




